Why is access control important?

Access controls limit access to information and information processing systems. When implemented effectively, they mitigate the risk of information being accessed without the appropriate authorisation, unlawfully and the risk of a data breach.
Describe an application that would need access control.

Access control is a fundamental component of security compliance programs that ensures security technology and access control policies are in place to protect confidential information, such as customer data
What is a role used for?

Role-based access control (RBAC) restricts network access based on a person’s role within an organization and has become one of the main methods for advanced access control. The roles in RBAC refer to the levels of access that employees have to the network
Why is role based access control more scalable than discretionary or mandatory access control?
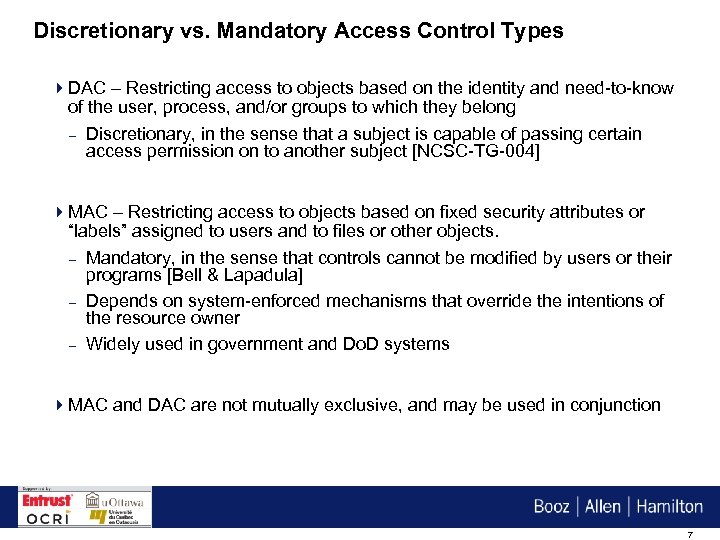
For most business applications, RBAC is superior to ACL in terms of security and administrative overhead. ACL is better suited for implementing security at the individual user level and for low-level data, while RBAC better serves a company-wide security system with an overseeing administrator.
| Term | Definition |
|---|---|
| Authorization | Authorization is the function of specifying access rights/privileges to resources, which is related to general information security and computer security, and to access control in particular. More formally, “to authorize” is to define an access policy |
| Role Based Access Control | Role-based access control (RBAC) restricts network access based on a person’s role within an organization and has become one of the main methods for advanced access control. The roles in RBAC refer to the levels of access that employees have to the network. |
| Capabilities | The definition of a capability is something that a person or thing is able to do. When a person can cook, this is an example of a situation where he has the capability to cook. When a computer can open a file, this is an example of a situation where the computer has the capability to open the file. |