Write the following steps in the correct order:
Receive access token
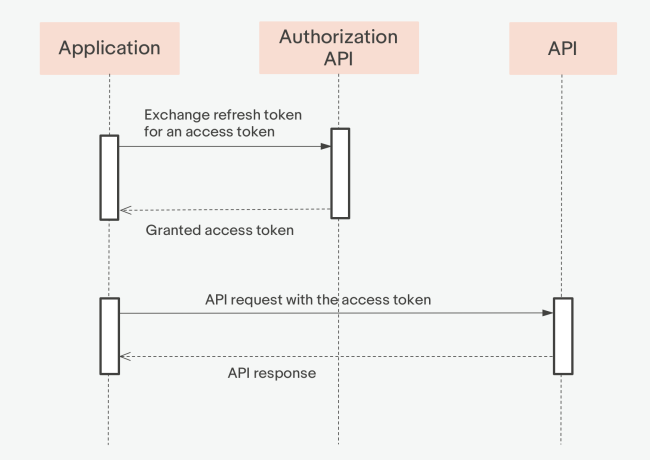 Once you have an authorization code, use the authentication service POST /oauth/token endpoint to obtain access and refresh tokens. You will use the access token to make API calls in a later step. Note: The obtained authorization code is only viable for two minutes.
Once you have an authorization code, use the authentication service POST /oauth/token endpoint to obtain access and refresh tokens. You will use the access token to make API calls in a later step. Note: The obtained authorization code is only viable for two minutes.
Redirect to a third party authentication endpoint
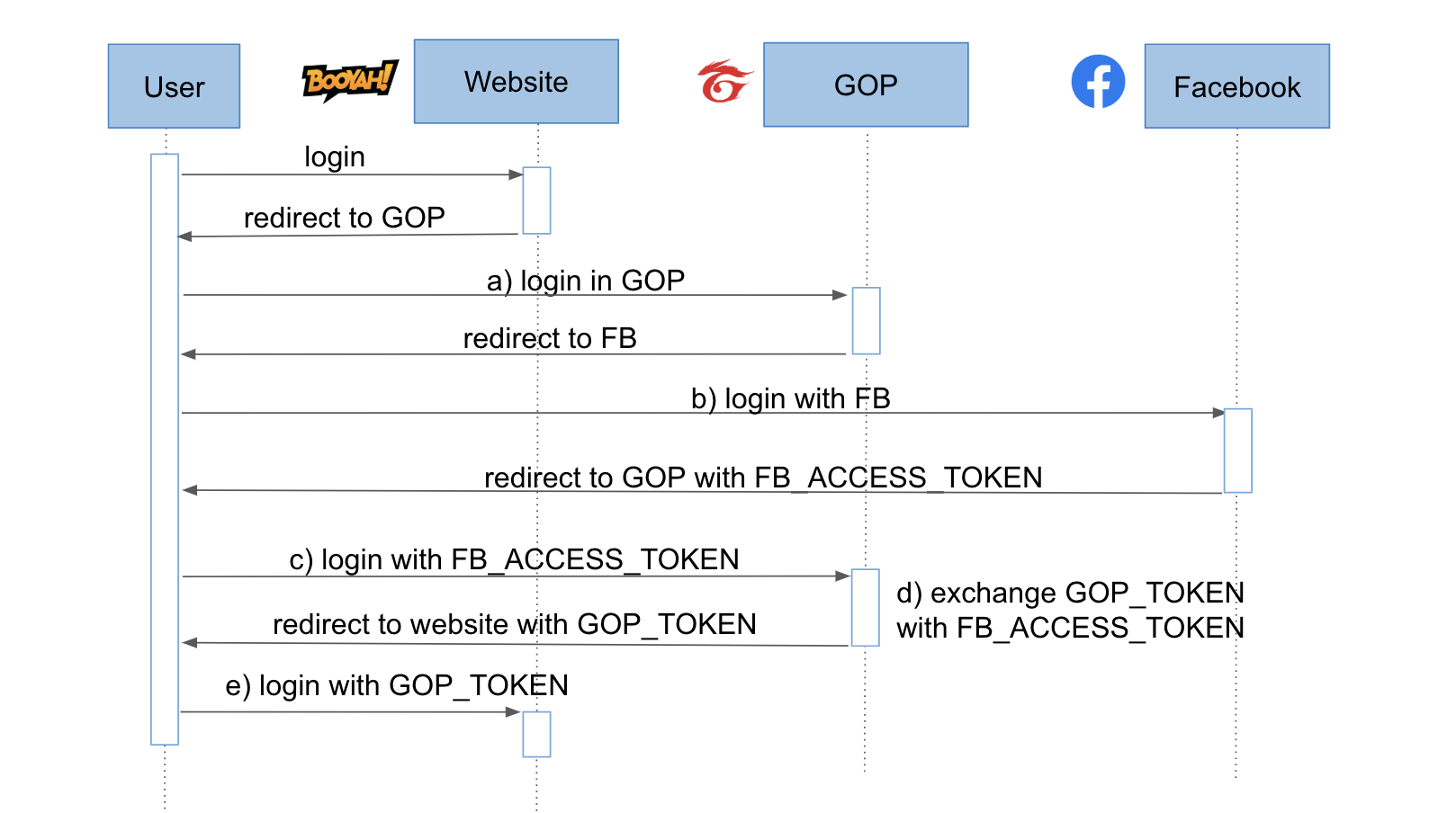 For example, if a user intends to access a protected page in your application, and that action triggers the request to authenticate, you can store that URL to redirect the user back to their intended page after the authentication finishes
For example, if a user intends to access a protected page in your application, and that action triggers the request to authenticate, you can store that URL to redirect the user back to their intended page after the authentication finishes
Register your application to get a client_id and client_secret
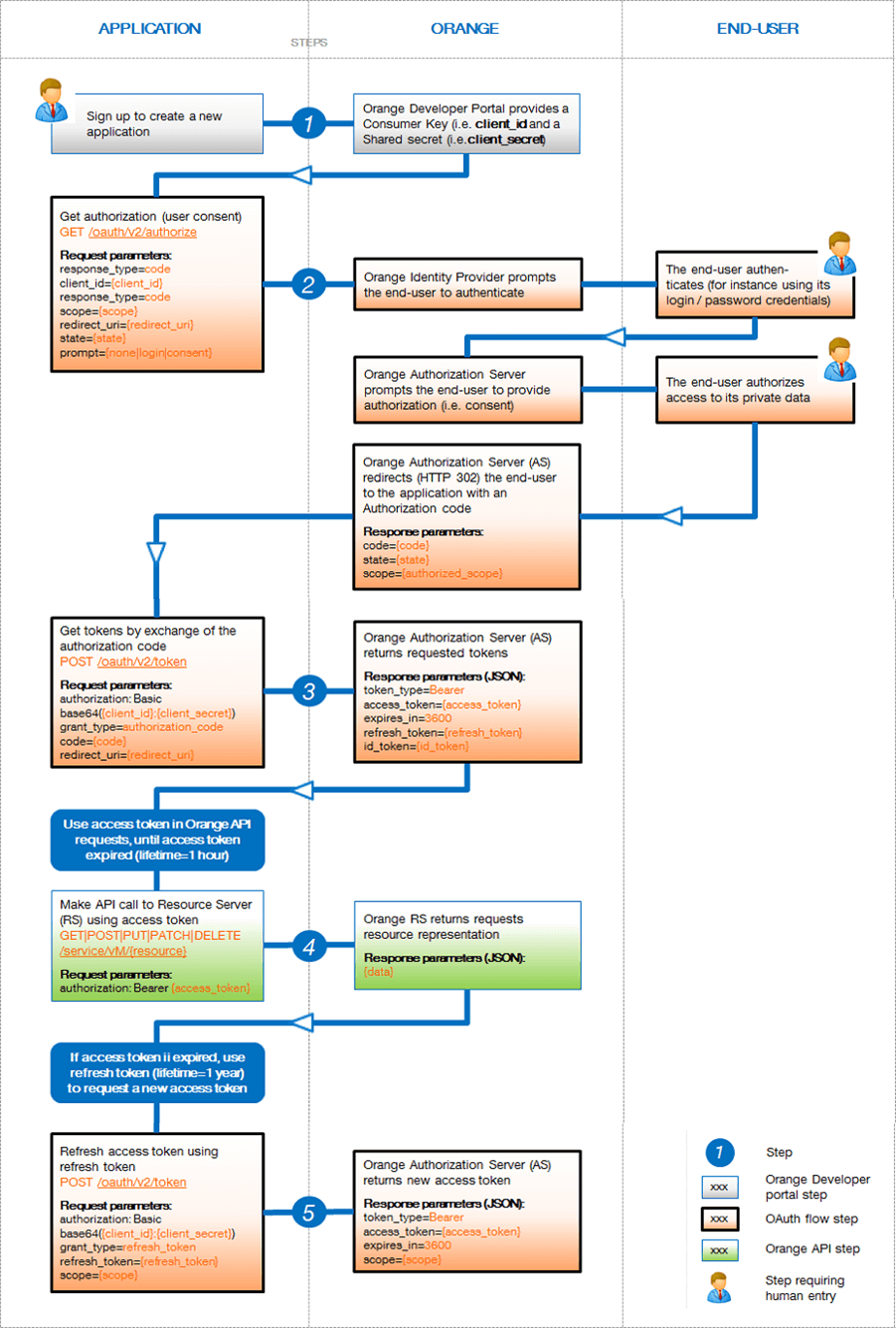 For example on Microsoft
For example on Microsoft
- Log in to the Microsoft Sharepoint Online account.
- Go to App Information
- Click Generate next to the Client Secret field.
- The value of the client secret is displayed in the Client Secret field.
- Click Create. The page redirects to the Microsoft Sharepoint Online page and the following message appears:The app identifier has been successfully created.The values of the client Id, client secret, title, and redirect URL are displayed.
Make a request to a third-party API endpoint
 When your application requests private data, the request must be authorized by an authenticated user who has access to that data. When your application requests public data, the request doesn’t need to be authorized, but does need to be accompanied by an identifier, such as an API key
When your application requests private data, the request must be authorized by an authenticated user who has access to that data. When your application requests public data, the request doesn’t need to be authorized, but does need to be accompanied by an identifier, such as an API key
Ask the client if they want to sign in via a third party
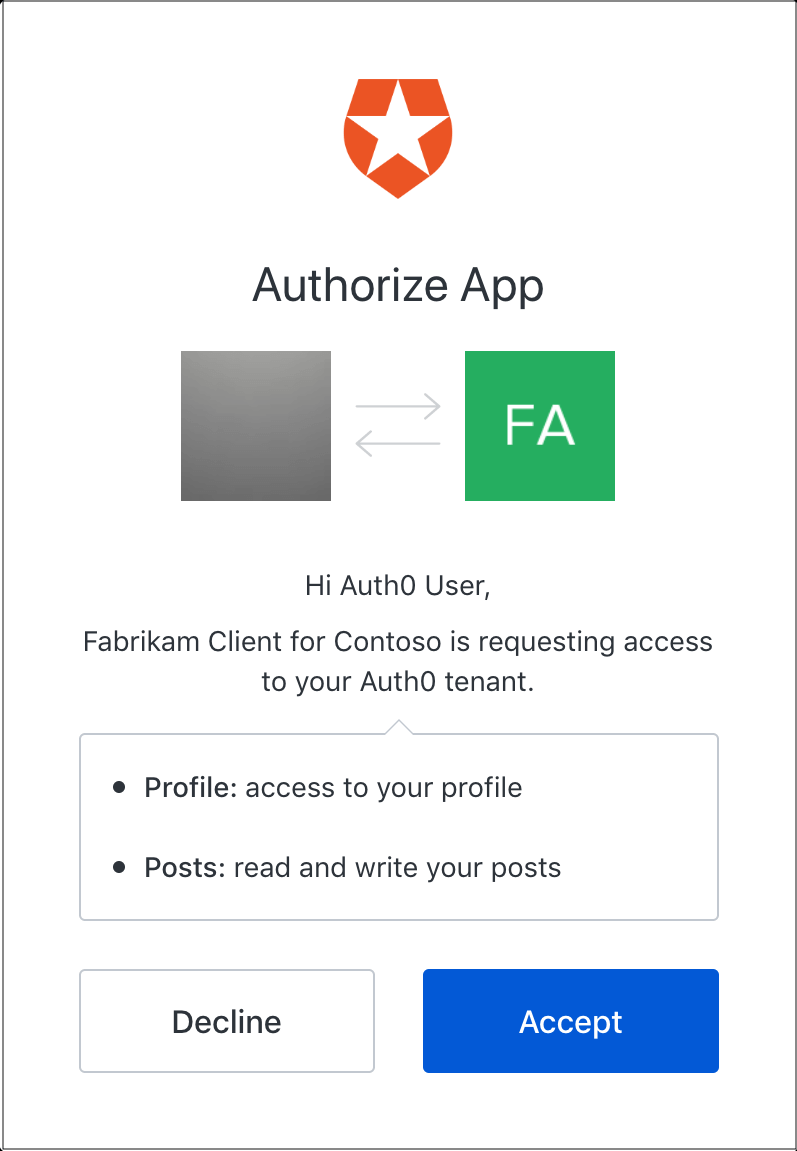
- Set up a basic Node.js project.
- Create a third party client.
- Choose your scopes.
- Redirect the user to Obtain a sipgate access token for a user. use the Provide a redirect endpoint to retrieve the authorization callback. server access token to communicate with our API.
- That’s it!
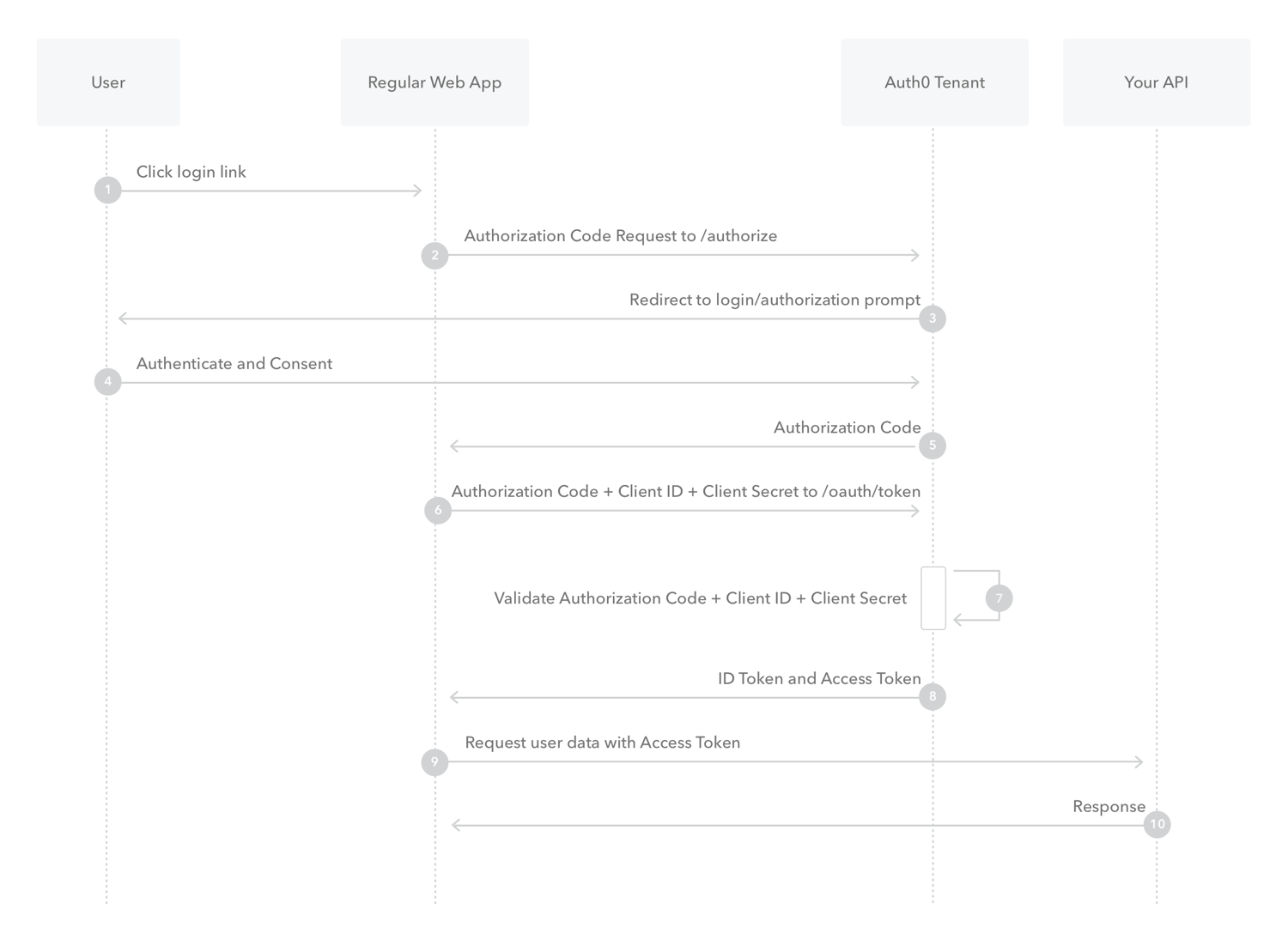
Receive authorization code

- User initiates the flow.
- User enters credentials.
- User gives consent.
- The login app sends a request Apigee Edge.
- Apigee Edge generates an authorization code.
- Edge sends the authorization code back to the client.
Make a request to the access token endpoint
 When you put a VerifyAccessToken policy at the front of your API proxy flow, apps must present a verifiable access token (also called a “bearer token”) to consume your API. To do this, the app sends the access token in the request as an “Authorization” HTTP header
When you put a VerifyAccessToken policy at the front of your API proxy flow, apps must present a verifiable access token (also called a “bearer token”) to consume your API. To do this, the app sends the access token in the request as an “Authorization” HTTP header
What can you do with an authorization code?
 An authorization code is an alphanumeric password that authorizes its user to purchase, sell or transfer items, or to enter information into a security-protected space
An authorization code is an alphanumeric password that authorizes its user to purchase, sell or transfer items, or to enter information into a security-protected space
What can you do with an access token?
 Access tokens are the thing that applications use to make API requests on behalf of a user. The access token represents the authorization of a specific application to access specific parts of a user’s data. Access tokens must be kept confidential in transit and in storage
Access tokens are the thing that applications use to make API requests on behalf of a user. The access token represents the authorization of a specific application to access specific parts of a user’s data. Access tokens must be kept confidential in transit and in storage
What’s a benefit of using OAuth instead of your own basic authentication?
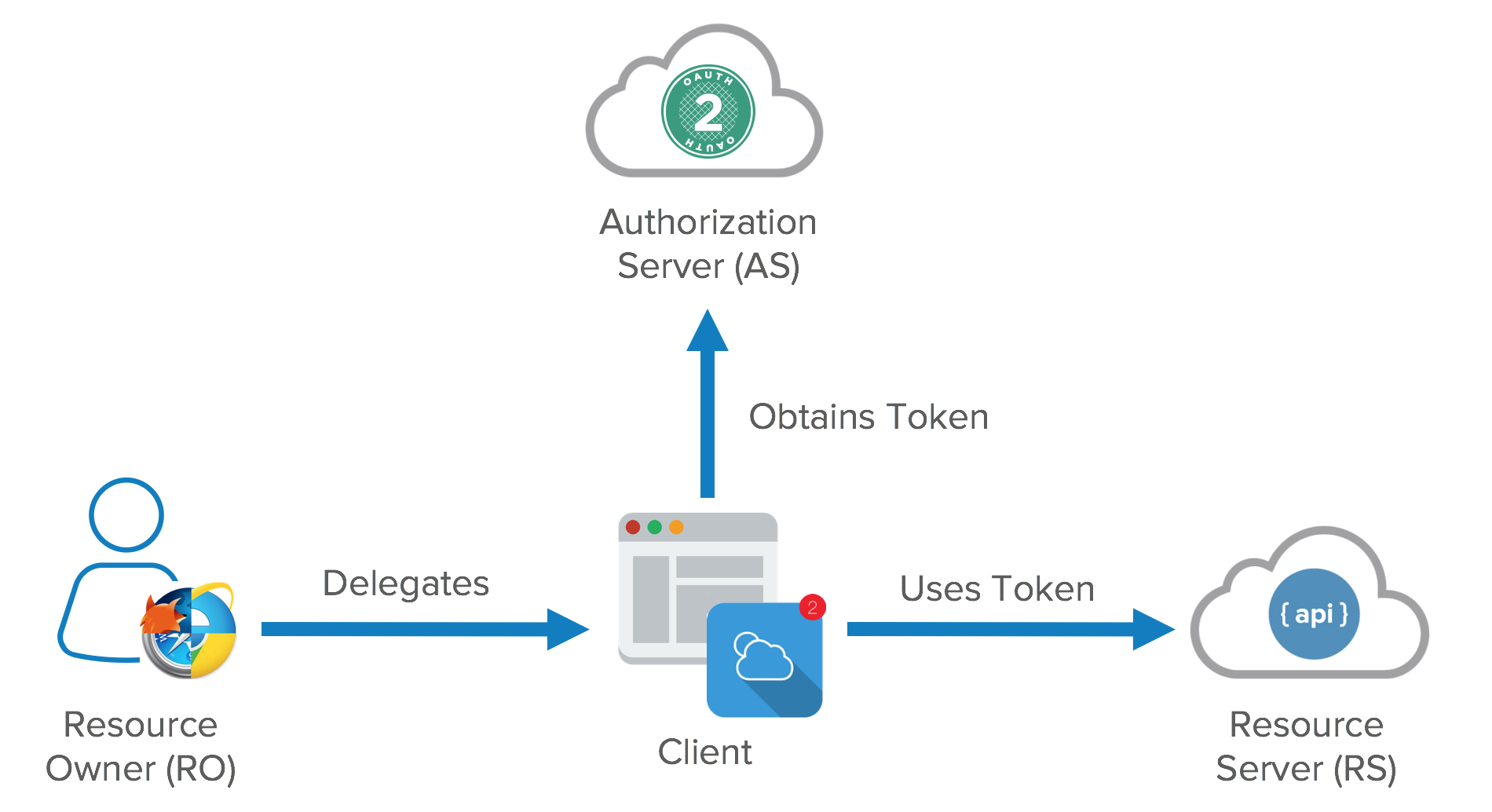 It enables apps to obtain limited access (scopes) to a user’s data without giving away a user’s password. It decouples authentication from authorization and supports multiple use cases addressing different device capabilities. It supports server-to-server apps, browser-based apps, mobile/native apps, and consoles/TVs
It enables apps to obtain limited access (scopes) to a user’s data without giving away a user’s password. It decouples authentication from authorization and supports multiple use cases addressing different device capabilities. It supports server-to-server apps, browser-based apps, mobile/native apps, and consoles/TVs
| Term | Definition |
|---|---|
| Client ID | Your client ID , also referred to as a UCI , is on all documents you get from us. It is an eight or ten-digit number that looks like this: 0000-0000 or 00-0000-0000. If you are applying to us for the first time, you will not yet have a client ID |
| Client Secret | A client secret is a secret known only to your application and the authorization server. It protects your resources by only granting tokens to authorized requestors. Protect your client secrets and never include them in mobile or browser-based apps. |
| Authentication Endpoint | Endpoint authentication is a security mechanism designed to ensure that only authorized devices can connect to a given network, site or service. The approach is also known as device authentication. … Authenticating both the user and the device can provide two-factor authentication (2FA). |
| Access Token Endpoint | The token endpoint is where apps make a request to get an access token for a user. This section describes how to verify token requests and how to return the appropriate response and errors. Authorization Code. Password Grant. Client Credentials. |
| API Endpoint | In endpoint is one end of a communication channel. When an API interacts with another system, the touchpoints of this communication are considered endpoints. For APIs, an endpoint can include a URL of a server or service. The place that APIs send requests and where the resource lives, is called an endpoint |
| Authorization Code | The authorization code is a temporary code that the client will exchange for an access token. The code itself is obtained from the authorization server where the user gets a chance to see what the information the client is requesting, and approve or deny the request. |
| Access Token | An access token is an object encapsulating the security identity of a process or thread. A token is used to make security decisions and to store tamper-proof information about some system entity. |